 We are in the early stages of creating projects and a research program that explores augmented team intelligence. ATI is about systems whose intelligence arises from the combined cognitive activities of teams of people and computers. When people with expertise in different areas work together, they can accomplish things that none of them could do on their own. Computers can also have advantaged abilities such as the ability to rapidly process large collections of information and the ability to systematically generate and evaluate solutions in combinatorial spaces. ATI seeks to create computer-supported teams that perform better than the best people or the best computers alone. For example, it can combine machine learning techniques working over big data with human subject matter experts in different areas to solve problems faster and more accurately than previously possible.
We are in the early stages of creating projects and a research program that explores augmented team intelligence. ATI is about systems whose intelligence arises from the combined cognitive activities of teams of people and computers. When people with expertise in different areas work together, they can accomplish things that none of them could do on their own. Computers can also have advantaged abilities such as the ability to rapidly process large collections of information and the ability to systematically generate and evaluate solutions in combinatorial spaces. ATI seeks to create computer-supported teams that perform better than the best people or the best computers alone. For example, it can combine machine learning techniques working over big data with human subject matter experts in different areas to solve problems faster and more accurately than previously possible.
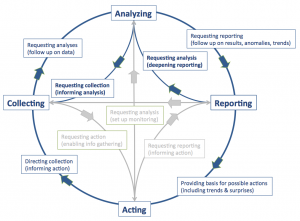 Intelligence analysis is an area with challenging problems that can be addressed by ATI. The figure on the left portrays an intelligence workflow as four activities. Collecting means gathering intelligence data, such as from electronic records, online sources and field reports. Analyzing means turning raw data into contextualized information relating adversarial goals, hypotheses and evidence. This includes spotting trends and anomalies, creating structures that relate data as evidence to hypotheses about events and transactions, and predicting plausible outcomes. Intelligence analysis is an interesting application in this area in part because of the variety of activities and roles that need to be coordinated.
Intelligence analysis is an area with challenging problems that can be addressed by ATI. The figure on the left portrays an intelligence workflow as four activities. Collecting means gathering intelligence data, such as from electronic records, online sources and field reports. Analyzing means turning raw data into contextualized information relating adversarial goals, hypotheses and evidence. This includes spotting trends and anomalies, creating structures that relate data as evidence to hypotheses about events and transactions, and predicting plausible outcomes. Intelligence analysis is an interesting application in this area in part because of the variety of activities and roles that need to be coordinated.
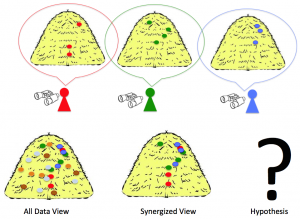 How could teams of people and computers be organized to work more effectively on intelligence analysis? The figure on the right illustrates an idea about focused attention-management and information sharing information across a team of analysts monitoring a region. Each analyst has a particular specialty, such as monitoring shipments to the area, or monitoring unfolding movements of people in large political or religious activities, or monitoring intelligence of various terrorist groups. Sometimes a significant event leaves signature traces along such different channels. The signal of a planned terrorist event, symbolized by the “?” in the example, is hidden in the noise and each analyst sees just a part of it. For example, suppose that there have been shipments of dual-use farm chemicals to the area that came to the attention of one analyst because the shipments were out of season and because they had potential dual use in making explosives. These shipments were delivered to a scattered group of people not known to be related by the first analyst. Suppose that a second analyst monitoring social interactions creates data about social networks. This analyst might have seen unusual patterns of communications across branches of the organization coordinating small rendezvous among agrarian members that are distantly linked and not typically in contact. Suppose that a third analyst monitoring upcoming gatherings on a religious holiday has monitored tips that suicide bombings are planned, but only vague details about which events or who is doing it. How could a system effectively bring together the three analysts to see the hidden pattern in the unfolding events, where the farm chemicals are being shipped to scattered points, gather together, and assembled into explosive devices to disrupt a gathering?
How could teams of people and computers be organized to work more effectively on intelligence analysis? The figure on the right illustrates an idea about focused attention-management and information sharing information across a team of analysts monitoring a region. Each analyst has a particular specialty, such as monitoring shipments to the area, or monitoring unfolding movements of people in large political or religious activities, or monitoring intelligence of various terrorist groups. Sometimes a significant event leaves signature traces along such different channels. The signal of a planned terrorist event, symbolized by the “?” in the example, is hidden in the noise and each analyst sees just a part of it. For example, suppose that there have been shipments of dual-use farm chemicals to the area that came to the attention of one analyst because the shipments were out of season and because they had potential dual use in making explosives. These shipments were delivered to a scattered group of people not known to be related by the first analyst. Suppose that a second analyst monitoring social interactions creates data about social networks. This analyst might have seen unusual patterns of communications across branches of the organization coordinating small rendezvous among agrarian members that are distantly linked and not typically in contact. Suppose that a third analyst monitoring upcoming gatherings on a religious holiday has monitored tips that suicide bombings are planned, but only vague details about which events or who is doing it. How could a system effectively bring together the three analysts to see the hidden pattern in the unfolding events, where the farm chemicals are being shipped to scattered points, gather together, and assembled into explosive devices to disrupt a gathering?
 Strategies and ground rules are always evolving when opposing sides compete. For example, in fraud detection, new schemes are developed by perpetrators to keep them below the detection radar. In intelligence situations, active terrorists try to carry out activities that will be effective but not detected before they are executed. When a new and effective technique gives an advantage to one side, that side will exploit the advantage until the other side is able to detect it and carry out preventive measures.
Strategies and ground rules are always evolving when opposing sides compete. For example, in fraud detection, new schemes are developed by perpetrators to keep them below the detection radar. In intelligence situations, active terrorists try to carry out activities that will be effective but not detected before they are executed. When a new and effective technique gives an advantage to one side, that side will exploit the advantage until the other side is able to detect it and carry out preventive measures.
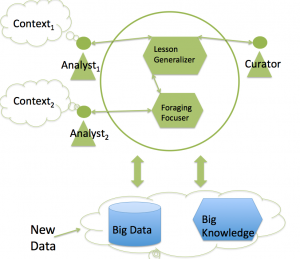
The system figures on the left sketches an architecture for a system addressing the “haystack” coordination scenario. This is for an operational system that automatically searches intelligence data for known patterns of dangerous activities by the opposition. The figure below is an architecture to enable a team and system to adapt quickly and effectively.
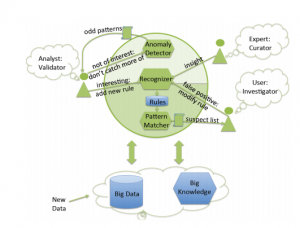 To keep up with an evolving enemy, a system needs to learn new dangerous activity patterns. In the haystack example, anomaly detection techniques can help to detect the outliers in shipments and activities. Detecting the overall pattern of transporting, assembling, and deploying explosives requires modeling the higher level plan with help from subject matter experts. To automate detection of such plans, the patterns used by the system need to be tuned to be sensitive enough to find hidden data while not giving too many false alarms that would overwhelm analysts with false leads. In the figure, the learning process involves specialists in different roles. Some analysts act as curators of training examples, bringing their subject matter expertise to the system. The team is orchestrated to train the system quickly and effectively, eliminating the advantage of new kinds of threat.
To keep up with an evolving enemy, a system needs to learn new dangerous activity patterns. In the haystack example, anomaly detection techniques can help to detect the outliers in shipments and activities. Detecting the overall pattern of transporting, assembling, and deploying explosives requires modeling the higher level plan with help from subject matter experts. To automate detection of such plans, the patterns used by the system need to be tuned to be sensitive enough to find hidden data while not giving too many false alarms that would overwhelm analysts with false leads. In the figure, the learning process involves specialists in different roles. Some analysts act as curators of training examples, bringing their subject matter expertise to the system. The team is orchestrated to train the system quickly and effectively, eliminating the advantage of new kinds of threat.
Some of our ongoing projects include precursors to CSI.
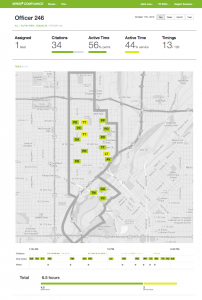 The Enforce project is an example of descriptive analytics to help urban departments of transportation understand both what is happening in the cities and also how the organizations should respond based on prescriptive analytics. In this project prescriptive analytics combine with collaboration and workflow in a digital nervous system that guides an department to understand its environment and to optimize its resources and performance. From one perspective, this is a modern version of organizational learning and intelligent workflow.
The Enforce project is an example of descriptive analytics to help urban departments of transportation understand both what is happening in the cities and also how the organizations should respond based on prescriptive analytics. In this project prescriptive analytics combine with collaboration and workflow in a digital nervous system that guides an department to understand its environment and to optimize its resources and performance. From one perspective, this is a modern version of organizational learning and intelligent workflow.
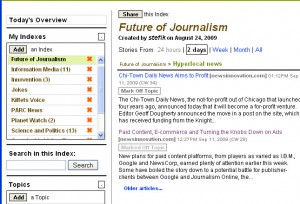 Another precursor to CSI is our work on social indexing. In this example, the system is trained to deliver specialized news according to the varied interests of different readers. The system coordinated the human work of publishers, curators and readers. It was trained by curators on individual topics to use good sources and to organize articles by topic. Users subscribed to channels of information curated by experts that they trusted. The system automatacally processed tens of thousands of articles per day and created customized digital news papers for people according to their interests.
Another precursor to CSI is our work on social indexing. In this example, the system is trained to deliver specialized news according to the varied interests of different readers. The system coordinated the human work of publishers, curators and readers. It was trained by curators on individual topics to use good sources and to organize articles by topic. Users subscribed to channels of information curated by experts that they trusted. The system automatacally processed tens of thousands of articles per day and created customized digital news papers for people according to their interests.
The March issue of IEEE Computer (volume 42 issue 3) has several papers on collaborative information seeking. This is one aspect of the area, but we find ourselves drawn more generally to sense making and analytics and to applications involving intelligence and big data. Particularly we are intrigued by combinations of human and machine learning as providing leverage for scalability as more people and computation resources are joined as a networked system. From a perspective of studying the processes of intelligence, these social systems provide opportunities based on visible and tangible activities, records of transactions and interactions, and external representations of intelligence in action.
Publications
 Stefik, Mark & Eldardiry, Hoda. (2014) Ganging Up on Big Data: Computer-Intermediated Collaborative Analysis. Collaborative Analysis and Reasoning Workshop at CTS 2014.
Stefik, Mark & Eldardiry, Hoda. (2014) Ganging Up on Big Data: Computer-Intermediated Collaborative Analysis. Collaborative Analysis and Reasoning Workshop at CTS 2014.
- Slides: Ganging Up on Big Data
 Stefik, M., Eldardiry, H., Pirolli, P., Lebiere, C., Cooper, J., Bobrow, D., Fritz, C., Gunning, D. (2014) Lessons Learned: Structuring, Abstraction, Diagnosis and Cognitive Modeling. Submitted to IARPA-RFI-14-01. January 10, 2014.
Stefik, M., Eldardiry, H., Pirolli, P., Lebiere, C., Cooper, J., Bobrow, D., Fritz, C., Gunning, D. (2014) Lessons Learned: Structuring, Abstraction, Diagnosis and Cognitive Modeling. Submitted to IARPA-RFI-14-01. January 10, 2014. Stefik, M. & Good, L. (2012) Design and Deployment of a Personalized News Service. AI Magazine, Vol 33, No. 2., pages 28-42.
Stefik, M. & Good, L. (2012) Design and Deployment of a Personalized News Service. AI Magazine, Vol 33, No. 2., pages 28-42.
